Avoiding Ad-Based Attacks Against Monero Users
Introduction
Malicious advertising is one of the most common ways Monero users are led to fake wallets, impersonation sites, and compromised downloads. These attacks do not exploit weaknesses in Monero itself, but instead rely on misplaced trust in search engine results and sponsored links.
This guide focuses on one specific scam vector: ad-based attacks. It explains how they work, why they are effective, and how to avoid them in practice. Understanding this pattern helps users make safer decisions across the broader Monero ecosystem.
For a higher-level explanation of how to evaluate trust and avoid scams more generally, see How to Evaluate Trust and Avoid Scams in the Monero Ecosystem .
How Ad-Based Attacks Work
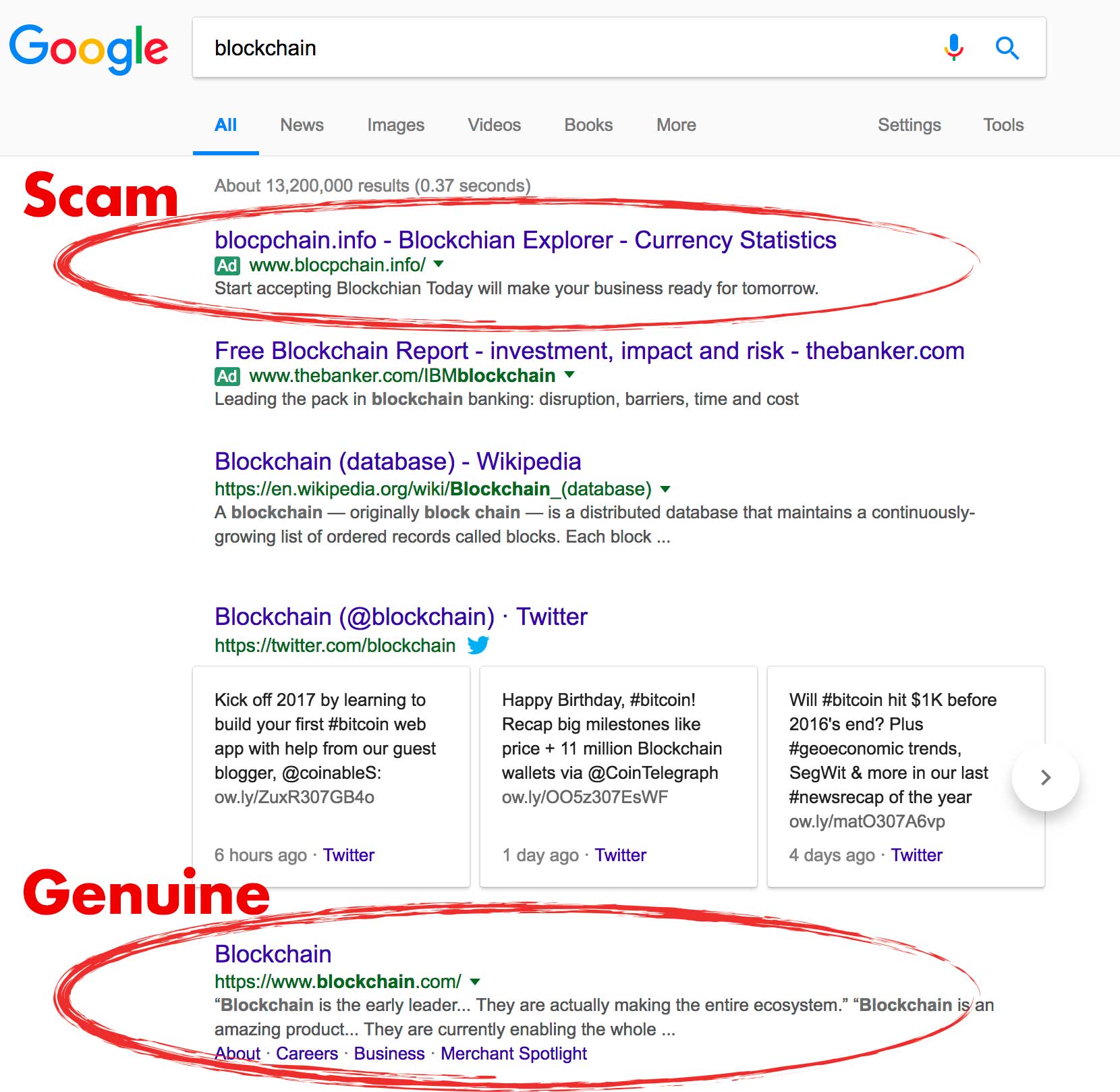
Search engines do not verify the authenticity of advertised websites. Anyone can pay to promote a link that appears above or alongside legitimate search results. Attackers take advantage of this by creating convincing copies of official-looking Monero pages.
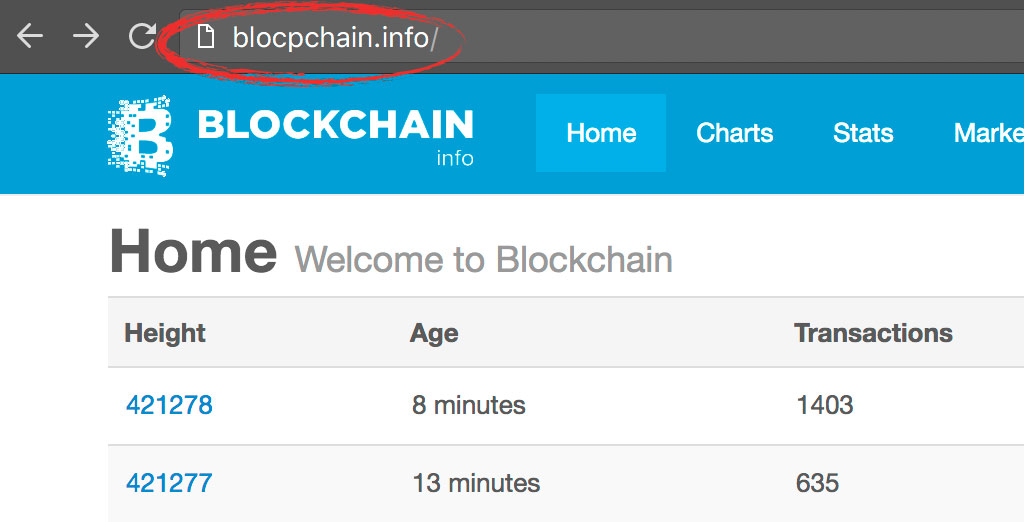
These ads often lead to sites that closely resemble real projects, sometimes using similar domain names, branding, and wording. The goal is to intercept users before they reach official sources.
Why Ads Are Not a Trust Signal
A common misunderstanding is that sponsored search results are safer or more legitimate because they appear prominently. In reality, ad placement is purely commercial and unrelated to technical trust or security review.
Ad-based attacks succeed because they exploit convenience and urgency. Users searching quickly for a wallet or download may click the first visible link without verifying its source.
In the Monero ecosystem, trust is established through verification, not visibility. Official software and documentation are published through well-known, stable channels such as getmonero.org, along with cryptographic signatures that can be checked independently.
Common Characteristics of Malicious Ads
- Sponsored links claiming to offer “official” Monero wallets
- Domains that closely resemble legitimate project names
- Urgent language encouraging immediate downloads or updates
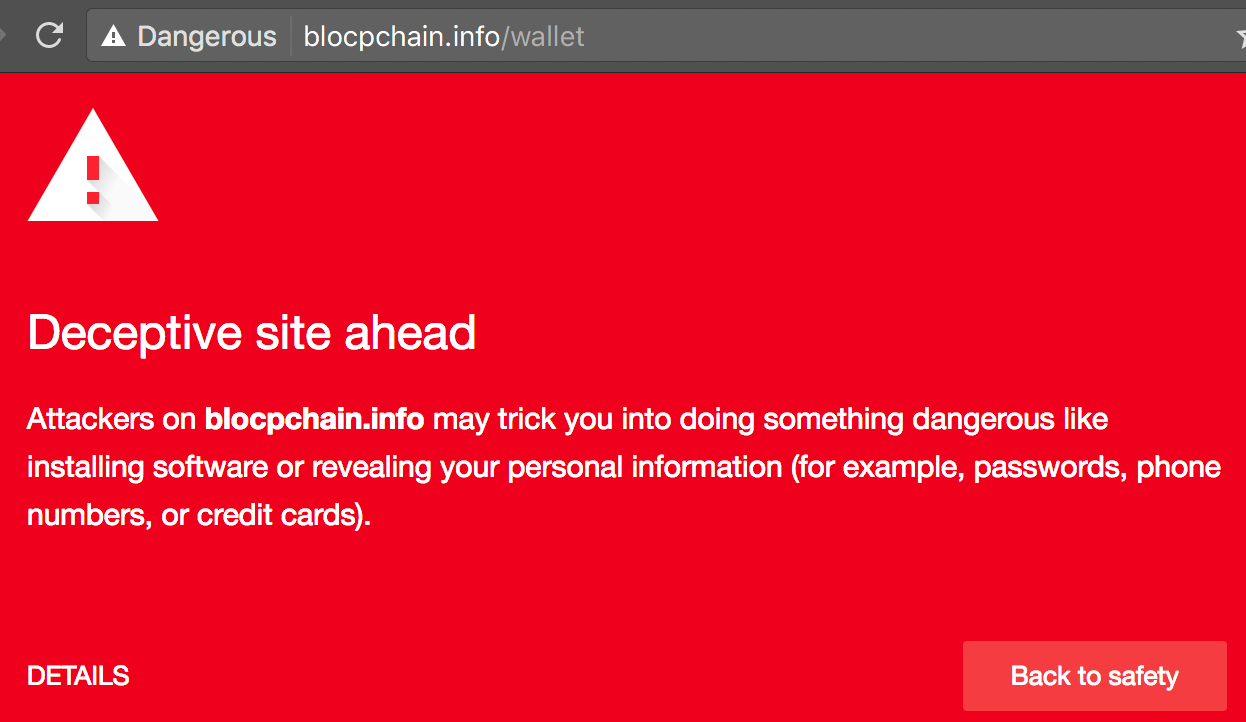
- Pages that omit or fake cryptographic verification information
These traits are not limited to a single campaign or year. While individual domains change frequently, the underlying pattern remains consistent.
How to Protect Yourself
The most effective defense against ad-based attacks is behavioral rather than technical. Avoid clicking sponsored results when searching for Monero-related software or documentation.
Instead, navigate directly to known official sources or use bookmarks you have previously verified. When downloading software, always verify hashes and signatures provided by the project.
How This Fits into a Broader Trust Model
Ad-based attacks are one example of a wider category of impersonation scams. They succeed when users substitute convenience or authority signals for verification.
Learning to recognize this pattern makes it easier to avoid other scams, including fake support accounts, cloned repositories, and unofficial third-party services.
This tutorial should be read as a practical case study within the broader trust framework outlined in How to Evaluate Trust and Avoid Scams in the Monero Ecosystem .

 monero.how
monero.how