How to Safely Hold Monero in Cold Storage

What is cold storage?
Cold storage is a term used by the cryptocurrency community to refer to a wallet which resides offline, disconnected from the Internet and therefore safe from hackers or other threats. Your Monero private keys never touch an internet-connected device, making them immune to remote attacks, keyloggers, and malware.
Why should I use cold storage?
If you hold a large amount of Monero which you have no plans to spend soon, cold storage can help you secure that value against attackers. Offline wallets are also useful if you wish for your loved ones to have access to your Monero in the event of your physical absence. For long-term holdings, cold storage provides the highest level of security available, as your funds remain completely isolated from online threats.
What equipment and software do I need?
The recommended approach is to use the official Monero wallet generator on an Internet-connected computer running TAILS. TAILS stands for "The Amnesic Incognito Live System". It is an operating system which runs from a USB drive and safely ensures that your computer is not compromised while the wallet generator is running, and that no trace of your private keys will remain on the computer when you power it off.
If you do not want to trust an Internet-connected machine using TAILS, you may also take additional precautions, such as buying a new laptop which has never touched the Internet just to use it for this purpose, or use an old PC or laptop without internet connection. You could then download the official generator on an Internet-connected computer, verify its GPG signature, and transfer it via USB drive to use on the air-gapped machine. Feel free to take whichever precautions fit your threat model, but this article will assume that you plan to use an Internet-connected computer running TAILS.
First, you'll need to follow the instructions to create a bootable TAILS USB drive. You will need two empty USB drives, each at least 8GiB in size. Installing TAILS is a good idea for two reasons:
- It is less likely that someone can serve you a compromised version of the wallet generator and steal your money.
- It is less likely that a hacker can spy on you and steal your Monero private keys.
Once you have installed and booted up TAILS, you can then prepare to generate your cold storage wallet. Have a pen and paper ready with a hard surface to write on (to make sure you don't leave behind any marks).
How do I download and verify the official wallet generator?
While you can use the official Monero wallet generator directly in your browser at web.getmonero.org/generator, the most secure approach is to download it for offline use. This ensures the generator code hasn't been tampered with and allows you to use it on an air-gapped computer.
On an internet-connected computer (or in TAILS before disconnecting), download the generator files from the official page. Look for the download link to wallet-generator.zip. Extract the zip file to a USB drive. The extracted folder contains wallet-generator.html, which is the file you'll open in a web browser.
For maximum security, you should verify the GPG signature of the generator to ensure it hasn't been modified. The official page provides signature verification instructions using GPG. If the signature check returns "Good signature," you can proceed with confidence. This verification step is optional but highly recommended for large holdings.
How do I actually create the cold wallet?
This is where it's time to get paranoid. Make sure you are in a private place and that your computing environment is secure. Ensure that there are no cameras in the vicinity and the line of sight to your computer screen is obscured as much as possible. Close the shades or blinds, throw a blanket over yourself, check for suspicious holes in the wall… sweep the area for vulnerabilities. You can't be too careful here.
Start up TAILS. If you're using the online version, get connected and navigate to web.getmonero.org/generator. If you downloaded the generator for offline use, open the wallet-generator.html file in the Tor Browser or Firefox. Ensure you're using the correct file and that the page loads properly.
When the generator loads, it will display options for creating different types of cryptocurrency wallets. Select Monero from the dropdown menu. A new, random Monero address will be generated automatically using your browser's cryptographically secure random number generator.
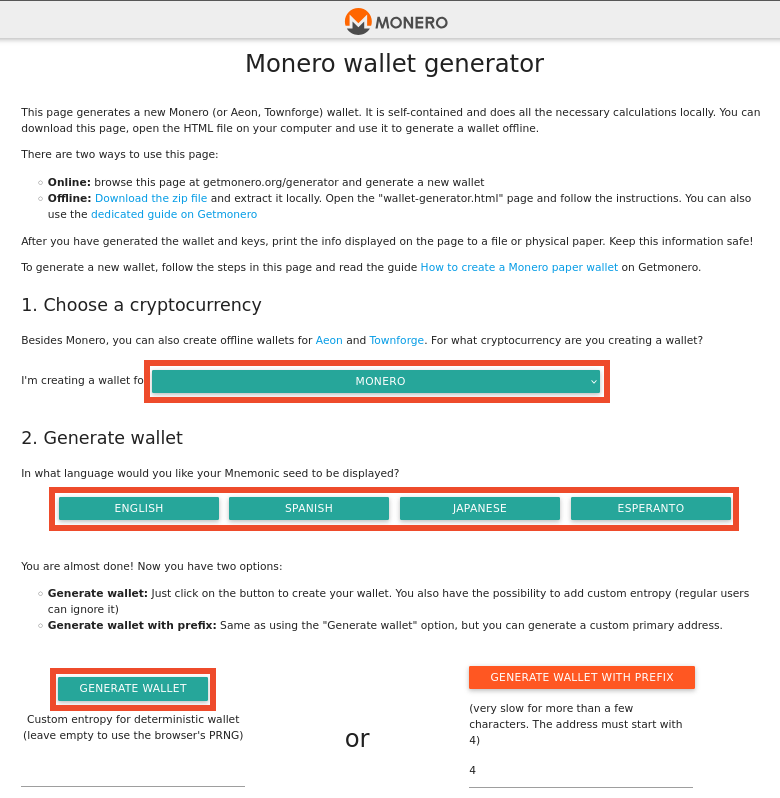
Fold your paper in half horizontally or use your own Monero paper wallet for secure offline storage. On the outside of the folded paper, carefully write down your public address (the long alphanumeric string starting with a "4" or "8"). This is the address you'll use to receive Monero. Double-check every character—one mistake means lost funds.
Open the paper and write down the 25-word mnemonic seed on the inside. This is critically important! This seed phrase is the master key that can regenerate both your public address and the private keys needed to spend your Monero. Guard it well. Never tell anyone your seed or allow them to discover it, and never type it into a computer (except to restore and spend your funds later, after making sure you trust the computer and wallet application you are using). If you lose this seed or if someone else obtains it, your money (and privacy!) could be lost forever.
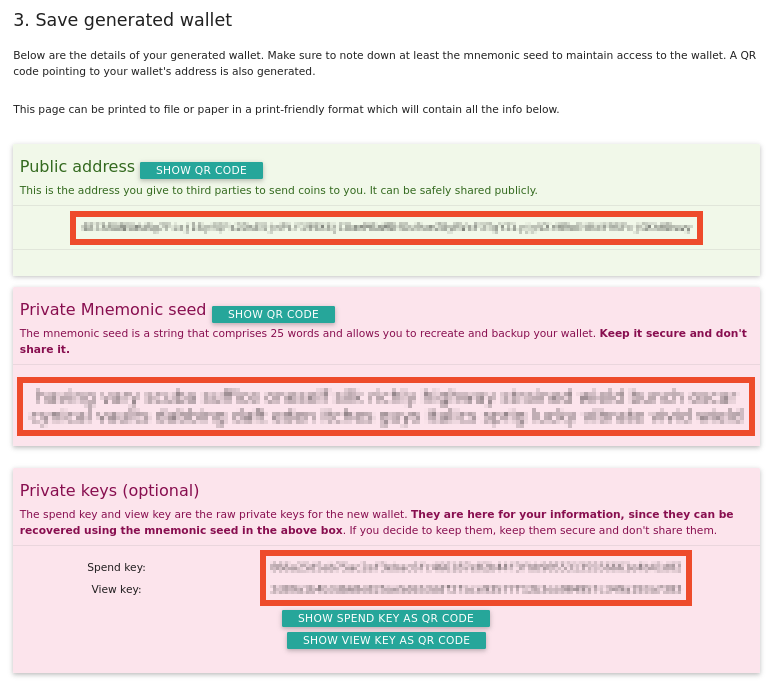
Check and re-check your work. Verify each word is spelled correctly and in the correct order. A single error makes recovery impossible.
Optionally, if you would like to use an online computer to watch for incoming transactions without exposing your spending ability (more on this below), you may also record the private view key. This key allows you to see incoming transactions to your wallet without being able to spend them.
Note that the view key should also be kept as secret as possible! While knowing this key will not allow anyone to move your coins, they will be able to watch all activity in your wallet, which leads to a loss of privacy. Only record the view key if you specifically need watch-only functionality.
Now, after you ensure your mnemonic seed (and optionally view key) is safely and accurately recorded, you may safely send funds to the public address (the long alphanumeric string that you wrote on the outside of the folded paper).
If you have followed these instructions as prescribed, you can be reasonably certain that your Monero is safe.
How can I check my wallet balance?
Firstly, if you are using Monero for its privacy functionality, know that exposing your view key to any online service will compromise your privacy. Second, it is not strictly possible to have a "watch-only wallet" in the same way as Bitcoin, because Monero's privacy features require some calculation with the spend key (which you keep offline). However, you can set up a view-only wallet using the Monero GUI or CLI wallet with your view key to monitor incoming transactions. Check this article for more information on using view keys.
How can I spend from my cold storage wallet?
You can find a guide to restoring your cold wallet to a connected client in this article. Note that once you do this, your funds are no longer as secure as the private keys have been exposed to an internet-facing machine. It is strongly recommended to send any large leftover amount of Monero to a new cold storage wallet once you have made your desired transactions. This practice of creating a fresh cold wallet for remaining funds is called "rotating" your cold storage.
This all seems very involved. Is there an easier way?
The good news is that hardware wallet support for Monero is now available, making cold storage more convenient than ever. Both Ledger (Nano S, S Plus, and X models) and Trezor (Model T, Safe 3, and Safe 5) now fully support Monero through integration with the official Monero GUI wallet or third-party wallets like Feather.
Hardware wallets provide an excellent balance of security and usability. Your private keys remain on the secure device and never touch your computer, even when signing transactions. While they require an upfront investment (typically $60-150 USD), they offer a more user-friendly experience than paper wallets for those who plan to make occasional transactions from cold storage.
For the absolute highest security with maximum simplicity for long-term storage you never plan to touch, a paper wallet created with the official generator remains an excellent choice. The paper wallet approach has no hardware cost, no firmware to update, and no electronic failure points—just make sure you store your seed phrase securely in multiple locations.
Frequently Asked Questions
Can I create multiple cold wallets for different purposes?
Yes, and this is actually a recommended security practice. You can create separate cold wallets for different purposes—for example, one for long-term savings that you never plan to touch, another for medium-term holdings you might access occasionally, and a third for funds you want family members to access in an emergency. Each wallet has its own unique seed phrase and address. By segregating your holdings, you reduce the risk that a single compromised wallet exposes all your funds. Common misunderstanding: You don't need separate computers or TAILS installations—you can generate multiple wallets in the same session, just make sure to record each seed phrase accurately and separately before generating the next wallet.
What happens if I lose my seed phrase?
If you lose your 25-word seed phrase and don't have a backup, your Monero is permanently lost—there is no recovery mechanism, no "forgot password" option, and no customer support that can help you. This is fundamentally different from traditional banking, where you can prove your identity to recover access. The reason for this permanence is that Monero's security model depends on you being the only person who knows your seed. No one else has a copy, not even the Monero developers. This is why backing up your seed phrase in multiple secure locations (fireproof safe, safety deposit box, trusted family member in a sealed envelope) is critical. The practical implication: treat your seed phrase with the same care you'd treat a large amount of physical cash—you wouldn't store $10,000 in just one location without backups. Common misunderstanding: writing your seed phrase on paper doesn't make it insecure; what makes it insecure is storing that paper in an obvious or vulnerable location, or showing it to others.
Is using the generator online less secure than using it offline?
Using the official Monero generator online (directly at web.getmonero.org/generator) while running TAILS is reasonably secure for most threat models, because TAILS isolates the browser and ensures no persistent storage of your keys after shutdown. The wallet generation happens entirely in your browser using JavaScript, and the seed is generated using your browser's cryptographically secure random number generator—no data is sent to any server. However, using the generator completely offline (downloaded, verified, and run on an air-gapped computer that has never touched the internet) provides the absolute highest security by eliminating any theoretical risk of network-based attacks during the brief moment the generator is running. The trade-off: the offline method requires more technical knowledge (downloading, verifying GPG signatures, transferring files via USB) but eliminates even remote possibilities of compromise. Practical implication: for holdings under $10,000 USD, TAILS + online generator is likely sufficient; for six-figure holdings or nation-state threat models, offline generation is worth the extra effort. Common misunderstanding: using the generator online doesn't mean your seed is "sent to a server"—the generation happens entirely locally in your browser, but the theoretical risk is that a sophisticated attacker could compromise your network connection during that brief session.
Should I use a password manager to store my seed phrase?
No. Storing your Monero seed phrase in a password manager (whether cloud-based like LastPass or 1Password, or local like KeePass) defeats the purpose of cold storage and introduces new attack vectors. Password managers are designed for convenience and routine access, not for cold storage of life-changing amounts of money. Cloud-based password managers are vulnerable to data breaches, account takeover, and company security failures (even well-regarded services have been breached). Local password managers are vulnerable if your computer is compromised by malware or if you forget your master password. The seed phrase for a cold wallet should be written on paper and stored in physically secure locations—this air-gaps your backup from digital attacks entirely. The practical implication: if you're using cold storage, you're accepting slight inconvenience (physically retrieving your paper backup) in exchange for maximum security. If you want convenience, consider using a hardware wallet with PIN protection for smaller amounts, and reserve pure cold storage (paper-only backup) for your largest holdings. Common misunderstanding: "encrypted password managers are just as secure as paper" ignores the fact that encrypted data can theoretically be brute-forced with sufficient computing power, whereas a properly hidden paper backup cannot be remotely accessed at all.
How do I know the official generator hasn't been compromised?
The official Monero wallet generator is open-source, meaning the code is publicly available for security researchers to audit. You can verify the generator's integrity by checking the GPG signature provided on the download page, which confirms the files were created by a known Monero developer and haven't been modified. When you verify the signature and see "Good signature," this cryptographic proof means the generator matches the official version. Beyond technical verification, you're also protected by the fact that any compromise of the official generator would be quickly detected by the Monero community, as thousands of security-conscious users and developers monitor the project. The practical implication: taking the extra few minutes to verify the GPG signature gives you cryptographic proof that you're using authentic software, rather than just trusting it. Common misunderstanding: "I can skip verification because getmonero.org is the official site" overlooks the possibility of your connection being intercepted (man-in-the-middle attack) or your DNS being compromised; GPG verification protects against these attack vectors by proving the file's authenticity regardless of how you obtained it.
Can I use the same cold wallet for receiving Monero multiple times?
Yes, you can safely reuse the same Monero cold wallet address for multiple incoming transactions. Unlike Bitcoin, where address reuse can reduce privacy, Monero's privacy features (stealth addresses and ring signatures) mean that receiving multiple payments to the same address does not meaningfully reduce your privacy. Each transaction still uses a one-time stealth address on the blockchain, so observers cannot link your transactions together just by watching the address. The only person who knows all the payments went to the same wallet is you (and the senders, if you gave them the same address). The practical implication: you can write your cold storage address once and use it for months or years without privacy concerns, which is much simpler than managing multiple receive addresses. However, keep in mind that anyone you give your address to could potentially collaborate to correlate that they're paying the same person—this is a social risk, not a cryptographic one. Common misunderstanding: "I need a new address for every transaction for privacy" is a Bitcoin practice that doesn't apply to Monero; Monero's privacy happens at the protocol level, not the address level.
What should I do if I think someone saw my seed phrase?
If you have any reason to believe someone may have seen, photographed, or recorded your 25-word seed phrase—even briefly—you should assume that cold wallet is compromised and act immediately. Do not wait to see if funds go missing. Generate a new cold wallet following the same process, and as quickly as possible, restore your potentially compromised wallet in the official Monero GUI or CLI wallet, and send all funds to your new cold wallet's address. Once the funds have moved and confirmed on the blockchain (typically 10-20 minutes for 10 confirmations), your funds are safe in the new wallet. Then destroy all records of the compromised seed phrase. The trade-off: acting quickly means accepting the inconvenience and transaction fee cost (typically around 0.0001-0.001 XMR) to move funds, but this is far better than the risk of total loss. Practical implication: if you dropped your seed phrase paper in public, if a security camera might have captured it, if you showed it to someone to "explain Monero," or if malware might have captured a screenshot while it was visible on screen, treat it as compromised. Common misunderstanding: "They only saw it for a second, they couldn't memorize 25 words" underestimates the risk of photographic memory, hidden cameras, or someone quickly taking a smartphone photo; better to be paranoid and safe than to rationalize inaction and discover later that funds were stolen.

 monero.how
monero.how