How to Configure OpenAlias to More Easily Share Your Monero Address
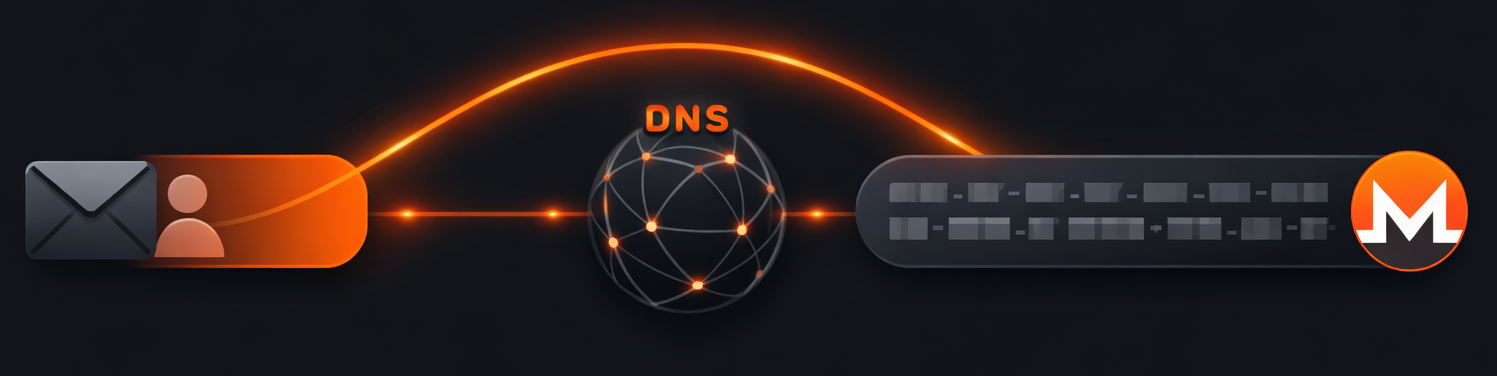
Overview
The Monero project created a simpler way to share your Monero public address. For example, our monero.how donation address is:
but OpenAlias allows us to configure our domain so that people can donate to us simply by entering hello@monero.how as the address to send to from a Monero wallet.
If you'd like to create your own OpenAlias address, you must own or control your own domain name. You cannot currently request that e.g. a gmail.com address have an OpenAlias associated with it. However, as the standard becomes more widely adopted, email providers may support this in the future.
What is OpenAlias?
OpenAlias is an open standard that makes cryptocurrency addresses human-readable by using the Domain Name System (DNS). Instead of memorizing or copying 95+ character Monero addresses, you can use familiar formats like email addresses or domain names.
At its core, OpenAlias is a TXT DNS record on a fully qualified domain name (FQDN). By combining this with DNS security technologies, it creates an aliasing system that is extensible for developers, intuitive for users, and works with both centralized and decentralized domain systems.
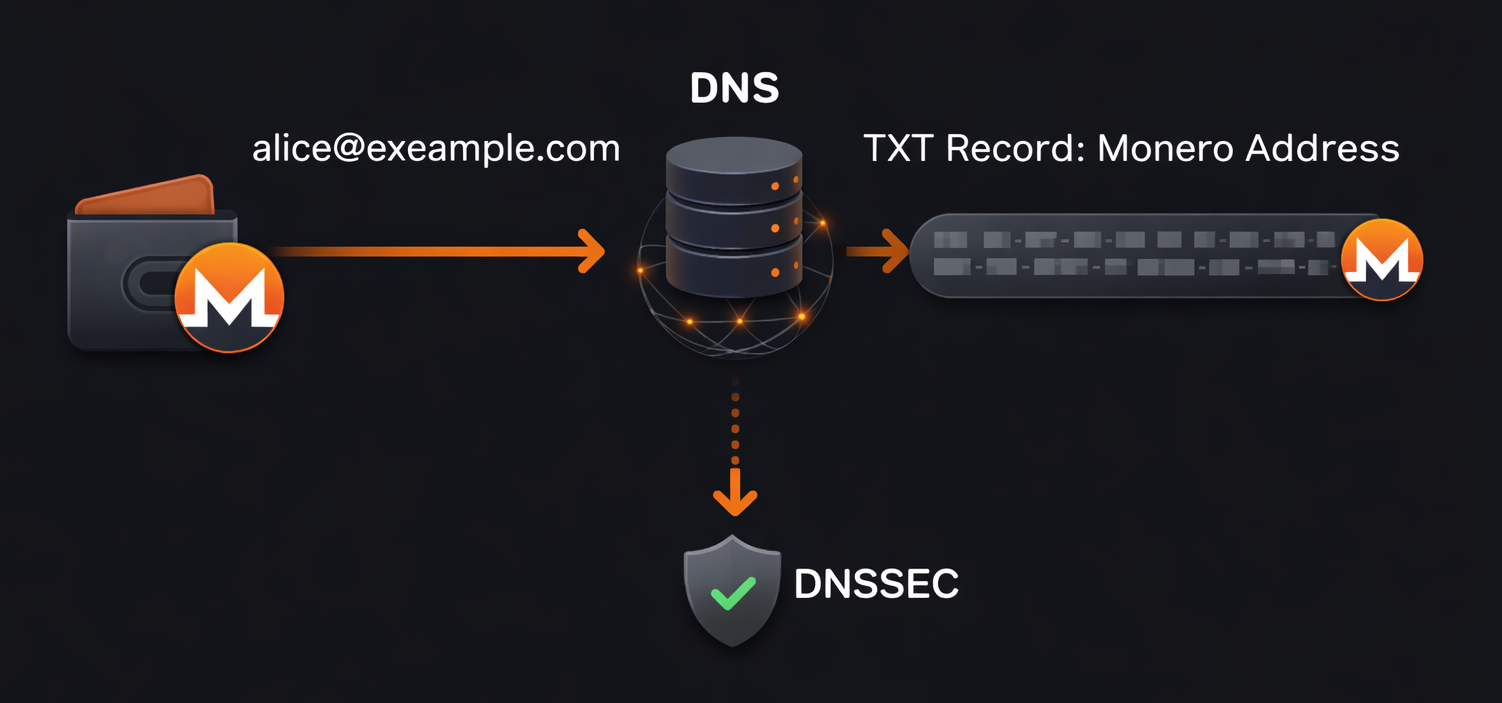
OpenAlias was developed by the Monero project but works with any cryptocurrency. Most Monero wallets including the official Monero GUI, Monero CLI, Cake Wallet, Monerujo, and Feather Wallet support OpenAlias natively. Some Bitcoin wallets like Electrum also support the standard.
Configuring Your DNS for OpenAlias
Let's say your email address is alice@example.com. OpenAlias automatically replaces the '@' sign with a '.' - which means that the configuration we are about to show you will allow payments to be sent to you at either 'alice@example.com' or at 'alice.example.com'.
Locate the DNS configuration for your domain name at the registrar you purchased it at, and add a TXT record for the host 'alice.example.com' with the following value (enter it all on one line without line breaks):
Important details about the TXT record:
- Replace the address with your actual Monero address
- Replace "Alice Lastname" with your name (this will appear in compatible wallets)
- The tx_description is optional but helps recipients identify the purpose
- Each key-value pair must end with a semicolon
- The record always starts with "oa1:xmr" to indicate OpenAlias Version 1 for Monero
If you are unfamiliar with DNS, note that if asked for a TTL value, it's fine to leave it at its default value. The TTL specifies the maximum number of seconds that your new DNS record will be cached for by people that query it.
Once you have configured your TXT record, it may take a few hours to propagate. You can check it is working correctly by using MXToolbox's DNS lookup tool to check the status of your TXT records.
Note that if you want to add a Bitcoin donation address as well, you can do this by adding another almost identical record except that it would start with 'oa1:btc' instead of 'oa1:xmr', and would obviously contain your Bitcoin public address instead of your Monero address.
DNSSEC: Why It Matters for OpenAlias
Because DNS traditionally lacks integrity checking, using OpenAlias with basic DNS alone creates a security risk: an attacker could potentially tamper with your DNS records and redirect payments to their own address.
DNSSEC (Domain Name System Security Extensions) addresses this by adding cryptographic signatures to DNS records. When enabled, DNSSEC allows anyone requesting your DNS records to cryptographically verify that the records have not been tampered with.
We strongly recommend only using OpenAlias if your DNS provider supports DNSSEC. Most reputable domain registrars and DNS hosting providers now support DNSSEC as of 2026, though it may need to be explicitly enabled in your account settings.
DNSSEC is typically not something you configure manually - your DNS provider will either support it (and handle the cryptographic key management automatically) or not. When choosing a domain registrar or DNS provider, check their documentation for DNSSEC support before committing to OpenAlias.
To verify if your domain has DNSSEC properly configured, you can use Verisign's DNSSEC Analyzer. When properly configured, compatible Monero wallets will indicate that your OpenAlias is "secure" when users attempt to send to it.
Frequently Asked Questions
Can I use OpenAlias without owning a domain?
Not directly with your own address, but some services offer OpenAlias hosting for a small fee. Services like xmr.ist and xmr.id allow you to register an alias (like yourname@xmr.ist) without owning a full domain. The trade-off is that you're trusting a third-party service to maintain the DNS records correctly and not change them maliciously. If you plan to receive significant amounts or want maximum control and security, owning your own domain with DNSSEC is the recommended approach. A common misunderstanding is that you can use any email address for OpenAlias - this only works if you control the domain's DNS records.
What happens if I change my Monero address after setting up OpenAlias?
One of OpenAlias's key advantages is flexibility - you can update your TXT record at any time with a new Monero address. Once the DNS change propagates (typically minutes to hours depending on your TTL settings), wallets will automatically resolve to your new address. The alias itself (like alice@example.com) never changes, which means you can keep using the same easy-to-remember identifier even if you rotate addresses for privacy or security reasons. Your TTL setting determines how quickly the change takes effect - a lower TTL means faster updates but slightly more DNS queries. A common misconception is that changing your address will "break" your OpenAlias - in reality, it's designed specifically to allow address updates without changing the alias.
Do all Monero wallets support OpenAlias?
Most modern Monero wallets support OpenAlias, including the official Monero GUI and CLI wallets, Cake Wallet, Monerujo, and Feather Wallet. However, wallet support isn't universal - some lightweight or web-based wallets may not implement the DNS lookup functionality required for OpenAlias. Before advertising your OpenAlias address for payments, verify that your intended recipients are using a compatible wallet. The easiest way to test this is to try sending a small test transaction using your OpenAlias in the wallet you plan to recommend. When OpenAlias works correctly, the wallet will display the full Monero address after resolving the alias, and may show a "secure" or "verified" indicator if DNSSEC is properly configured. A common misunderstanding is assuming all cryptocurrency wallets support OpenAlias - in practice, it's primarily a Monero ecosystem feature with limited Bitcoin wallet support (mainly Electrum).
Is OpenAlias safe to use for receiving large payments?
OpenAlias security depends entirely on whether DNSSEC is enabled for your domain. With DNSSEC properly configured, OpenAlias provides strong cryptographic guarantees that the resolved address hasn't been tampered with - comparable to HTTPS for websites. Without DNSSEC, OpenAlias is vulnerable to DNS hijacking attacks where an attacker could potentially redirect payments by poisoning DNS caches or compromising DNS servers. For large or critical payments, verify that: (1) your domain has DNSSEC enabled and properly configured, (2) the recipient's wallet shows a "secure" or "verified" indicator when resolving your alias, and (3) you're using a reputable DNS provider with strong security practices. Additionally, consider having recipients verify the resolved address through a secondary channel (like messaging the full address directly) for high-value transactions. A common misunderstanding is that OpenAlias is "just as secure as regular addresses" - in reality, it adds a DNS layer that must be properly secured to maintain the same security guarantees.
Conclusion
OpenAlias provides a practical solution to one of cryptocurrency's most persistent usability problems: addresses that are impossible to memorize and difficult to communicate. By leveraging DNS infrastructure you may already control, you can create memorable, human-friendly payment identifiers without sacrificing security - provided you enable DNSSEC.
While OpenAlias adoption is primarily concentrated in the Monero ecosystem, the open standard can work with any cryptocurrency. As more wallets implement support and DNS providers make DNSSEC easier to enable, human-readable cryptocurrency addresses may become the norm rather than the exception.
For your next steps, consider exploring how to use the Monero GUI wallet to test sending to an OpenAlias address, or learn more about running your own Monero node for enhanced privacy.

 monero.how
monero.how